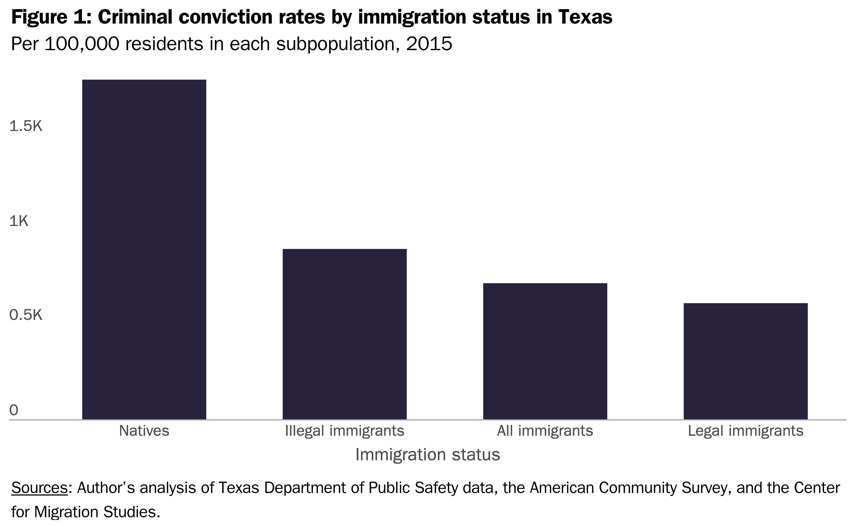
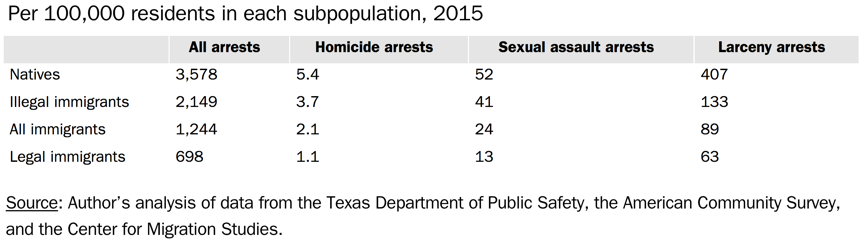
Male impotence, substance abuse, right-wing politics, left-wing politics, sexually transmitted diseases, cancer, mental health.
Those are just a few of the advertising labels that Google’s adtech infrastructure routinely sticks to Internet users as it watches and tracks what they do online in order to target them with behavioral ads.
Intimate and highly sensitive inferences such as these are then systematically broadcast and shared with what can be thousands of third party companies, via the real-time ad auction broadcast process which powers the modern programmatic online advertising system. So essentially you’re looking at the rear-end reality of how creepy ads work.
This practice is already the target of a legal complaint in Europe, filed under the bloc’s General Data Protection Regulation (GDPR).
The real-time bidding (RTB) complaint, which was lodged last fall by Dr Johnny Ryan of private browser Brave; Jim Killock, previously director of the Open Rights Group; and Michael Veale, a data and policy researcher at University College London, alleges “wide-scale and systemic breaches of the data protection regime by Google and others” in the behavioral advertising industry.
It argues the personalized ad industry has “spawned a mass data broadcast mechanism” which gathers “a wide range of information on individuals going well beyond the information required to provide the relevant adverts”; and also that it “provides that information to a host of third parties for a range of uses that go well beyond the purposes which a data subject can understand, or consent or object to”.
“There is no legal justification for such pervasive and invasive profiling and processing of personal data for profit,” the complaint asserts.
The individuals filing the complaints have now submitted additional evidence showing lists of ad categories used by Google and online ad industry association, the Internet Advertising Bureau (IAB), that they say show sensitive inferences are systematically made.
The documents, reviewed by TechCrunch, are supplementary evidence for the two original complaints filed with the UK’s ICO and the Irish DPC last year.
The complaint action has also now been joined by Polish anti-surveillance NGO, the Panoptykon Foundation — which has notifies its local DPA of what it describes as “massive GDPR infringement”.
“Ad auction systems are obscure by design,” said Katarzyna Szymielewicz, president of the NGO in a statement. “Lack of transparency makes it impossible for users to exercise their rights under GDPR. There is no way to verify, correct or delete marketing categories that have been assigned to us, even though we are talking about our personal data. IAB and Google have to redesign their systems to fix this failure.”
Ravi Naik, partner at ITN Solicitors, who is working with the complainants, also added in a statement: “Panoptykon’s submissions add to the increasing focus on real time bidding. The complaint builds on our work before the UK ICO and Irish DPC. We foresee a cascade of complaints to follow across Europe, and fully expect an EU-wide regulatory response”.
The three content taxonomy documents that have been submitted as evidence include one used by Google and two compiled by the IAB to provide publishers with lists of ad categories.
The pair make the lists available online for publishers to download, though there’s no suggestion general Internet users are encouraged to take a look at how their online activity is sliced and diced into ad categories in order that their attention can be sold off to the highest bidder.
And while plenty of the ad categories look harmless enough — hatchback cars, pets, poetry, and so on — others, such as the ones we’ve flagged above, can be highly intimate and/or sensitive.
In Europe such sensitive data categories constitute what’s considered special category personal data — which refers to the most sensitive types of personal data, including medical information, political affiliation, religious or philosophical views, sexuality and information revealing racial or ethnic origin.
Multiple types of this special category data appear to be included in the content taxonomy lists we’ve reviewed.
Under GDPR, processing special category data generally requires explicit consent from users — with only very narrow exceptions, such as for protecting the vital interests of the data subjects (and, well, trying to sell Viagra isn’t going to qualify).
The original complaints argue that Internet users are unlikely to be aware such labels are being routinely stuck on them, let alone how widely their personal data is being shared with third parties participating in programatic ad auctions that rely on scale for the system to function.
The RTB process does not offer Internet users an opportunity to consent to each and every personal data transaction. If it did, web browsers would be swamped with creepy requests to process intimate information about them from scores of unfamiliar companies. And there’s no reason to think people would be okay with that.
“The speed at which RTB occurs means that such special category data may be disseminated without any consent or control over the dissemination of that data. Given that such data is likely to be disseminated to numerous organisations who would look to amalgamate such data with other data, extremely intricate profiles of individuals can be produced without the data subject’s knowledge, let alone consent,” the group write in their original complaint filing.
“The industry facilitates this practice and does not put adequate safeguards in place to ensure the integrity of that personal (and special category) data. Further, individuals are unlikely to know that their personal data has been so disseminated and broadcast unless they are somehow able to make effective subject access requests to a vast array of companies. It is not clear whether those organisations have a record of compliance with such requests. Without action by regulators, it is impossible to ensure industry-wide compliance with data protection regulations.”
They cite a New Economics Foundation’s estimate which suggests ad auction companies broadcast intimate profiles about an average UK internet user 164 times per day, adding: “Tracking IDs and other personally specific information are not actually necessary for ad targeting but allow you to be reidentified and profiled every day.”
Here’s a few more highly sensitive labels that are being attached to web users’ identities and shared with potentially thousands of bidding ad companies: Special needs kids, endocrine and metabolic diseases, birth control, infertility, diabetes, Islam, Judaism, disabled sports, bankruptcy.
These categories come from v2 of the IAB’s content taxonomy.
The group has also submitted v1 of the IAB’s taxonomy as evidence, and this includes other disturbingly intimate categories — including a category for ‘incest/abuse support’.
The IAB claims to have depreciated the v1 list but the complainants say it’s still being used in the IAB’s latest ad auctioning system.
We’ve reached out to the IAB Europe for comment.
Filing this new evidence, the complainants argue it underlines “the unreasonable degree of intimacy of the personal data broadcast in ad auctions”.
“The evidence we file today illustrates that the IAB and Google ad auction system can broadcast remarkably intimate details about what you watch, listen to, and read online. ‘Special category’ personal data like this enjoys special protections in the GDPR. I believe this raises the stakes of our complaint,” Brave’s Ryan told TechCrunch.
“Actors in this ecosystem are keen for the public to think they are dealing in anonymous, or at the very least non-sensitive data, but this simply isn’t the case. Hugely detailed and invasive profiles are routinely and casually built and traded as part of today’s real-time bidding system, and this practice is treated though it’s a simple fact of life online. It isn’t: and it both needs to and can stop,” added Veale in a statement.
The original IAB lists can be downloaded as a spreadsheet here (see tab 2 for the v1 list; and tab 1 for v2). While PDF versions of the IAB lists with special category and sensitive data highlighted can be viewed here (v1) and here (v2).
Google’s original document can be downloaded here from developers.Google.com. (A marked up version highlighting the special category data is also available from Brave here.)
We’ve also reached out to Google for comment on the latest development in the complaint.
After being sent the category lists for review, an ICO spokesperson told us: “The ICO and our partner authorities on the European Data Protection Board are already engaged on various issues relating to Google and we are engaging with the industry more widely. We are considering the concerns that have been raised with us.”
The agency has made online behavioral advertising a key priority, noting in its Technology Strategy that it’s probing web and cross device tracking, and citing examples including device fingerprinting, browser fingerprinting and canvas fingerprinting.
“This is likely to continue as more devices connect to the internet (IoT, vehicles etc) and as individuals use more devices for their online activities,” it writes in the strategy document. “These new online tracking capabilities are becoming more common and pose much greater risks in terms of systematic monitoring and tracking of individuals, including online behavioural advertising. The intrusive nature of the technologies in combination drives the case for this to be a priority area.”